HACKING
To master the Cyberpunk 2077 Breach ProtocolBreach Protocol In Cyberpunk 2077, Breach Protocol is a hacking mini-game used to gain rewards from terminals and access points, or to debuff enemies by uploading "daemons" (programs) onto their network. To play, you enter sequences of codes on a grid within a time limit to match the required daemon codes, aiming to select sequences that complete multiple daemon goals for better loot or effects. minigame, plan your path before starting, aiming for multiple daemon uploads by finding overlapping code sequences. Hovering over codes highlights matching numbers on the grid, which you select in alternating row and column patterns. Invest in Intelligence perks like Head Start and Compression and use a CyberdeckCyberdeck In Cyberpunk 2077, a Cyberdeck is a piece of cyberware that functions as a personal computer, acting as your primary interface for the game's hacking system, or "Netrunning". It allows players to use Quickhacks to remotely control devices, overload enemy cyberware, cause malfunctions, and even spread effects between enemies to deal damage, gain information, or distract them. Each Cyberdeck is designed for different playstyles and offers unique bonuses to RAM recovery, hack speed, or the spread and cost of Quickhacks. with a larger buffer to complete all daemons. If a puzzle is too difficult, exit and restart for a new challenge.
Planning Your Path
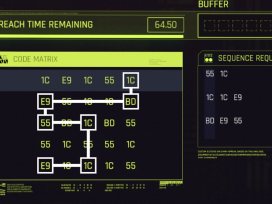
- Scan and Plan: Before the timer starts, hover over the desired sequences in the code matrix. This highlights all possible matching numbers in the grid on the left, allowing you to plan a path for the row-column-row pattern.
- Aim for Multiple Daemons: Look for a short, efficient code sequence that can fulfill the requirements for more than one daemon simultaneously. This increases your rewards.
- Refresh the Puzzle: If the code matrix doesn’t offer a viable solution for multiple daemons, or you get stuck, quit the breach and restart the access point. The grid will regenerate with a new sequence.
Executing the Breach
- Alternate Row and Column: Select a starting code from the top row. The next choice must be from the same column as your previous selection. Continue alternating between rows and columns to fill the input buffer.
- Utilize the Buffer: The buffer represents the number of inputs you have for the current sequence. Your chosen Cyberdeck and Intelligence perks will influence the size of the buffer.
- Be Aware of Your Position: While time moves slowly during scanning, it doesn’t stop. Make sure you are hidden so you aren’t spotted by security.
Enhancing Your Abilities
- Invest in Intelligence Perks: Perks from the Intelligence tab are essential.
- Head Start: Automatically uploads the first daemon, reducing the number of inputs needed.
- Compression: Reduces the number of inputs required for each daemon, making it easier to upload all of them.
- Upgrade Your Cyberdeck: A Cyberdeck with a larger buffer allows you to fit more characters and input more codes in a single breach.
Additional Tips
- Use Ping: Ping can help you locate access points in an area, showing connected devices with digital lines.
- Prioritize Access Points: Make it a rule to always start an encounter with a Breach Protocol, even if not planning to be stealthy. This can reduce the RAM cost of your other quickhacks.
Practice makes perfect
Fan-Made Recreation of “Breach Protocol” Mini-Game

Direct link to the game: https://www.cyberpunk-breach-protocol.com/